Decoding Obfuscated Stack Traces
While symbol renaming makes software code harder to understand, it also makes the task of maintaining and troubleshooting an obfuscated application more difficult. After you apply symbol renaming and ship your software, error reports received from customers will contain obfuscated stack trace information instead of the names given to them by the developers.
For example, if you have an obfuscated application that you have shipped and then received a stack trace from one of your customers, that stack trace might look like this:
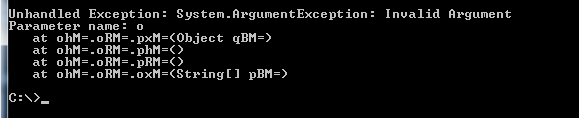
Agile.net solves this problem by generating XML-based map files each time you decide
to use symbol renaming to protect your software. The map file contains information
about the original types, methods, properties and events used in the source code
and the names given to them during the symbol renaming process.
When receiving an
error report containing stack trace information from a customer, the map file is
used to translate the obfuscated stack trace to its original form.
Using the decode stack trace form
To decode an obfuscated stack trace:
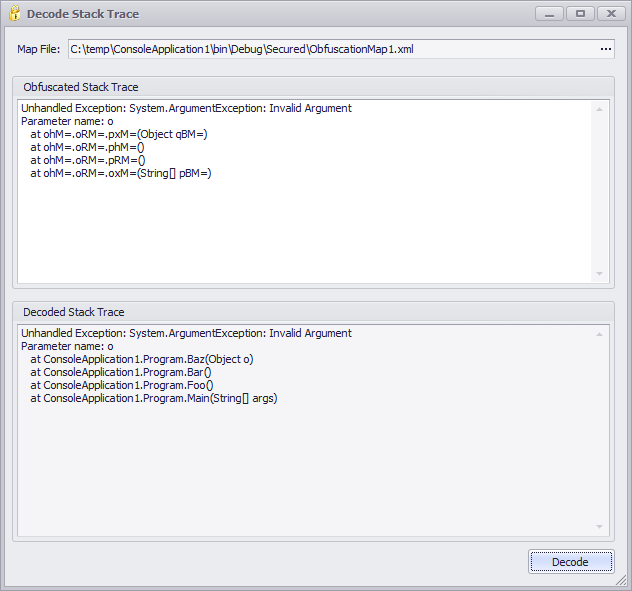
- Open the decode stack trace form by pressing the decode stack trace button located on the main ribbon bar.
- Select the map file generated when you protected your software. The map file is located in the protected assemblies output folder.
- Paste the stack trace into the text box labeled obfuscated stack trace.
- Press decode.
- The translated stack trace appears in the text box labeled decoded stack trace.