Features built to help you secure your revenues
Agile.NET, Powerful Code Protection, Obfuscation, and Licensing Solution for your .NET Apps
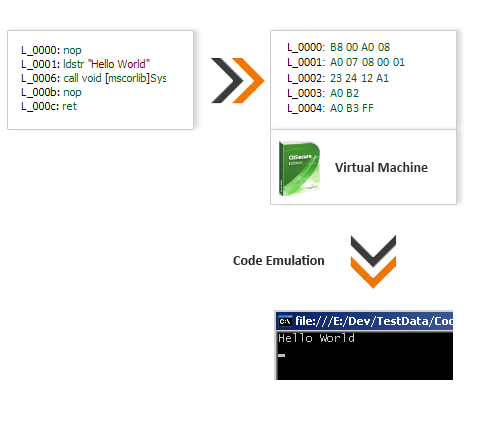
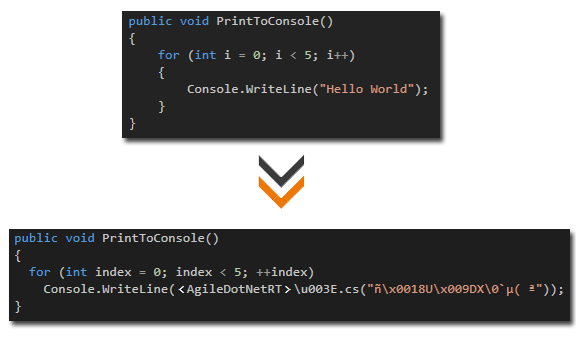
Code Virtualization
Code virtualization will convert your MSIL code into Virtual Opcodes that will only be understood by a secure Virtual machine. As opposed to protecting MSIL code through encryption where the encrypted code must be decrypted back into MSIL before it can be executed by the CLR, Code Virtualization use a Secure Virtual Machine which directly processes the protected code in the form of a Virtual Machine Language.
Method Level Code Encryption
Encrypts all the MSIL code and keeps it in a secure storage. When the assembly is loaded Agile.NET binds to the .NET runtime engine and manages decrypting the MSIL on a per method basis. Agile.NET creates a runtime environment that executes the original MSIL code by decrypting one method at a time, this important virtue minimizes the exposure of MSIL code in memory thus prevents dumping the code from physical memory.
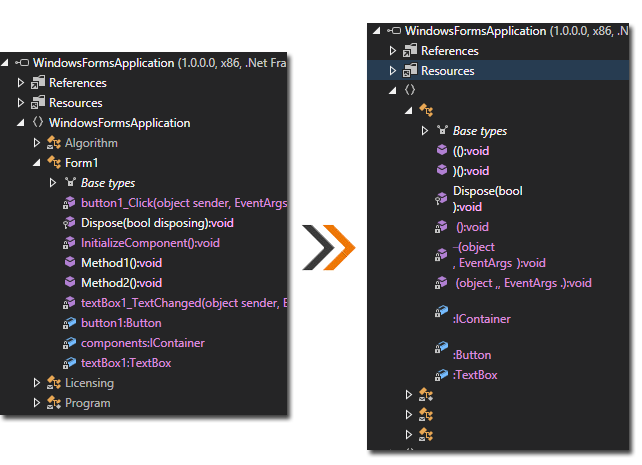
Entity Renaming
Renames metadata symbols including: class, field, method, properties, method parameters and generic parameter names to irreversible names that have no semantic meaning.
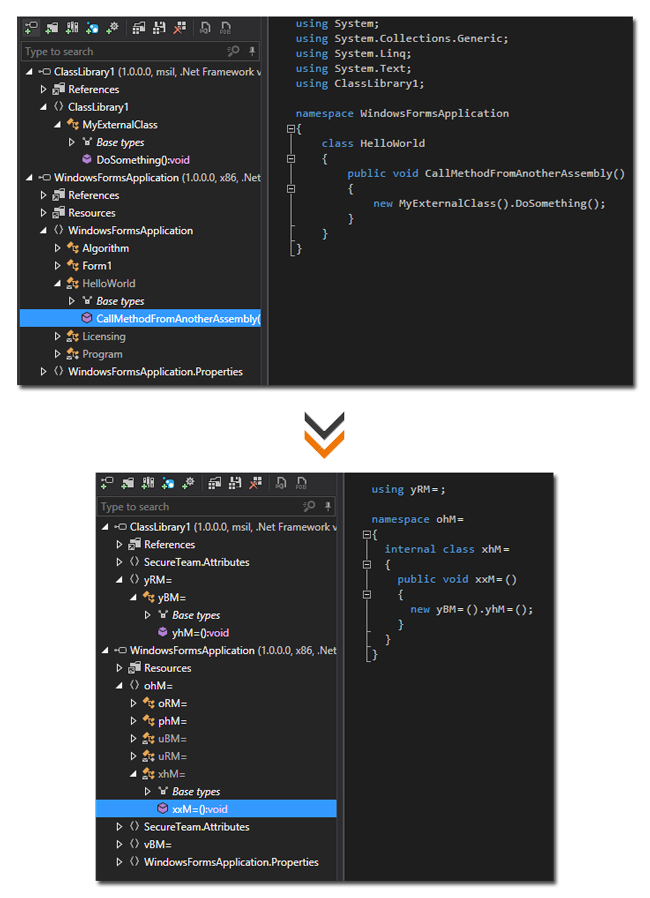
Cross Assembly Obfuscation
Allows renaming of external references thus dramatically increasing the number of renamed constructs. For instance, if class A declared in assembly A is referenced from assembly B and Agile.NET renames class A to A1, it will also rename B's external reference from A to A1.
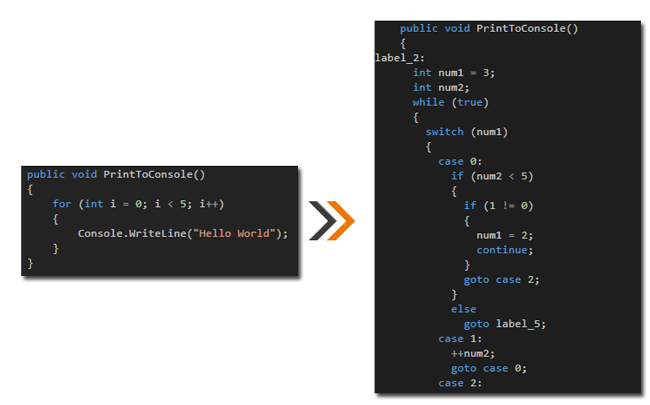
Control Flow Obfuscation
Hides the code flow of the program by transforming existing code flow patterns to semantically equivalent constructs, however different than the code originally written. The control flow obfuscation algorithm converts the original implementation into spaghetti code thus making it extremely harder to infer program logic. Agile.NET ensures that application code flow of the obfuscated assembly remains intact.
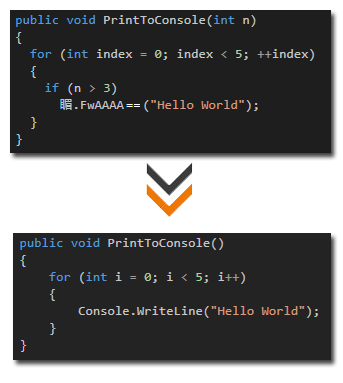
Method Call Obfuscation
Replaces calls to external members with dynamic methods created at runtime. The actual call is made using the method's metadata token rather than the method's name, this make it harder to understand the application's logic as it is no longer possible to browse through the code flow using standard reflector tools. Use this method to hide away external calls to the .NET class library as well as calls to methods declared in assemblies developed by your company and referenced from within an obfuscated assembly.

Assembly Merging
Merging allows a set of assemblies to be combined into a single file. This can be used to merge an executable file with its supporting dynamic linked libraries (DLLs) to allow you to distribute a runnable program as a single file. It can also be used to simplify large libraries that would otherwise include multiple DLLs with each needing to be referenced from the project that utilizes them. Merging reduces the total size of the deployment and improves the application load time because the windows loader doesn't have to load lots of dll files.
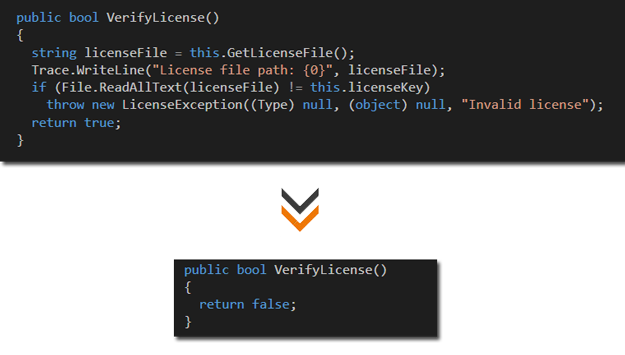
String Encryption
A common attacker will often search deployed assemblies for strings containing keywords such as 'GetLicense' or 'Invalid License'. By locating such strings, hackers attempt to circumvent the license protection embedded in the product they are hacking. Agile.NET transforms strings used in the source code into encrypted strings, the strings are decrypted on the fly when needed.